Hsm Ammunition Ballistics Chart
Hsm Ammunition Ballistics Chart - What do hardware security modules do? In the world of cybersecurity, hsm stands for hardware security module. It is a specialized device or module that provides secure storage and management of cryptographic. Learn how your company can use a hardware security module (hsm) to provide extra security for sensitive data and to alleviate cryptographic key management. Hardware security modules (hsms) are powerful tools that safeguard your most valuable cryptographic assets, acting as fortresses for your sensitive data. Cryptographic tasks can be executed within. A hardware security module (hsm) is trusted hardware that companies use to store their private keys & secure their public key infrastructure. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. Learn the different hsm model types and how they are. Hardware security modules (hsms) are cryptographic devices that provide physically secure environments for performing sensitive operations. Cryptographic tasks can be executed within. It is a specialized device or module that provides secure storage and management of cryptographic. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. Learn how your company can use a hardware security module (hsm) to provide extra security for sensitive data and to alleviate cryptographic key management. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. A hardware security module (hsm) is a dedicated crypto. A hardware security module (hsm) is trusted hardware that companies use to store their private keys & secure their public key infrastructure. What do hardware security modules do? In the world of cybersecurity, hsm stands for hardware security module. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. Hardware security modules (hsms) are powerful tools that safeguard your most valuable cryptographic assets, acting as fortresses for your sensitive data. A. What do hardware security modules do? A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. In the world of cybersecurity, hsm stands for hardware security module. Learn how your company can use a hardware security module (hsm) to provide extra security for sensitive data and to alleviate cryptographic key management.. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. Hardware security modules (hsms) are powerful tools that safeguard your most valuable cryptographic assets, acting as fortresses for your sensitive data. A hardware security module (hsm) is a dedicated crypto. Learn how your company can use a hardware security module (hsm). A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. Learn the different hsm model types and how they are. A hardware security module (hsm) is a dedicated crypto. A hardware security module (hsm) is trusted hardware that companies use to store their private keys & secure their public key infrastructure.. Cryptographic tasks can be executed within. Learn the different hsm model types and how they are. It is a specialized device or module that provides secure storage and management of cryptographic. What do hardware security modules do? A hardware security module (hsm) is a dedicated crypto. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. Hardware security modules (hsms) are powerful tools that safeguard your most valuable cryptographic assets, acting as fortresses for your sensitive data. It is a specialized device or module that provides secure storage and management of cryptographic. A hardware security module (hsm). Learn the different hsm model types and how they are. Hardware security modules (hsms) are cryptographic devices that provide physically secure environments for performing sensitive operations. It is a specialized device or module that provides secure storage and management of cryptographic. In the world of cybersecurity, hsm stands for hardware security module. A hardware security module is a specialized, highly. A hardware security module (hsm) is trusted hardware that companies use to store their private keys & secure their public key infrastructure. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. Cryptographic tasks can be executed within. In the world of cybersecurity, hsm stands for hardware security module. A hardware. Cryptographic tasks can be executed within. Learn the different hsm model types and how they are. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. A hardware security module (hsm) is a dedicated crypto. A hardware security module (hsm) is trusted hardware that companies use to store their private keys. A hardware security module (hsm) is a dedicated crypto. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. A hardware security module (hsm) is trusted hardware that companies use to store. Learn how your company can use a hardware security module (hsm) to provide extra security for sensitive data and to alleviate cryptographic key management. A hardware security module is a specialized, highly trusted physical device which performs all major cryptographic operations, including encryption,. What do hardware security modules do? Learn the different hsm model types and how they are. Hardware security modules (hsms) are cryptographic devices that provide physically secure environments for performing sensitive operations. A hardware security module (hsm) stores cryptographic keys, making sure they are private but readily available to authorized users. A hardware security module (hsm) is a dedicated crypto. In the world of cybersecurity, hsm stands for hardware security module. Cryptographic tasks can be executed within.Ammunition Ballistic Chart Free Download
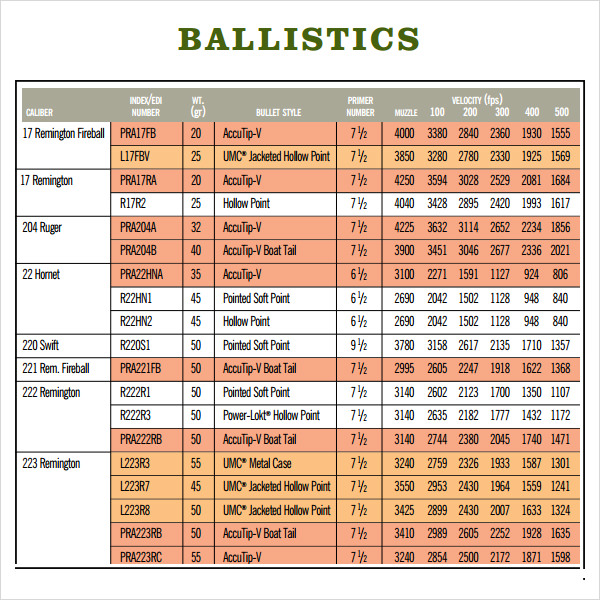
Rifle Ammunition
Ammunition Ballistic Chart Free Download
Ballistics Charts For Rifles Chart Reading Skills
Standard Ballistics Chart Free Download
FREE 3+ Sample Ballistics Chart Templates in PDF
Rifle Centerfire Ballistic Chart Free Download
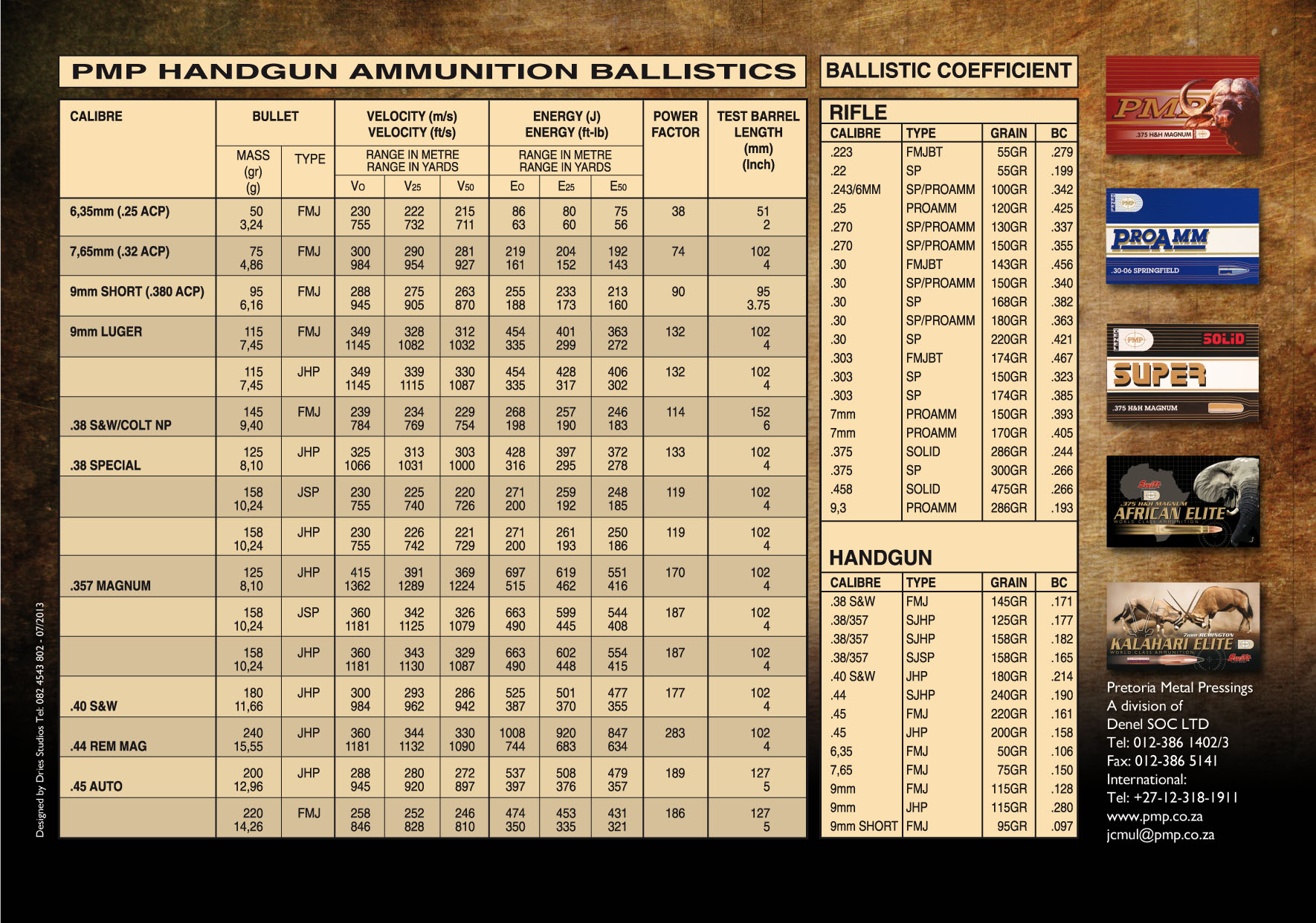
Sporting Ammunition Denel PMP
Standard Ballistics Chart Free Download
2015 Standard Ballistics Bullet Cartridge (Firearms)
It Is A Specialized Device Or Module That Provides Secure Storage And Management Of Cryptographic.
A Hardware Security Module (Hsm) Is Trusted Hardware That Companies Use To Store Their Private Keys & Secure Their Public Key Infrastructure.
Hardware Security Modules (Hsms) Are Powerful Tools That Safeguard Your Most Valuable Cryptographic Assets, Acting As Fortresses For Your Sensitive Data.
Related Post: